After five years of making, root file operation finally lands in the Dolphin file manager of KDE Plasma desktop. Here’s how to use Dolphin with root access.
The reason was apparent. Unless you know, the root file operation was the only critical feature not available in the famous Dolphin file manager. The developers didn’t want new users to play around in the file system with root privileges. That is not good for a stable system.
You get a prompt below if you try to open Dolphin today with the superuser. It is permanently disabled in the Dolphin code for uid=0.
Executing Dolphin with sudo is not possible due to unfixable security vulnerabilities.
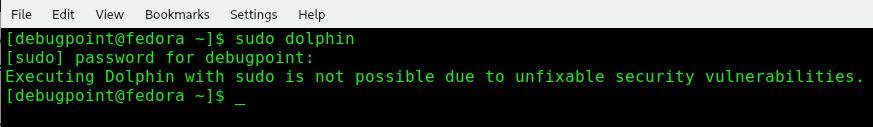
Table of Contents
A Little History of Dolphin with superuser privileges
You may need to access specific removable drives, files, and network shares via file manager at any given workflow, which requires admin privileges. But without the Dolphin built-in support, it is difficult today unless you are experienced enough to try out specific hacks (like the below), which have been popular until now.
The following famous command executes polkit to give necessary privileges to Dolphin.
pkexec env DISPLAY=$DISPLAY XAUTHORITY=$XAUTHORITY KDE_SESSION_VERSION=5 KDE_FULL_SESSION=true dolphin
The users request the feature many times via bug reports in forums. And several controversial extensions are created, such as Open Dolphin as Root (https://store.kde.org/p/1384645/) or Root action service menu (https://store.kde.org/p/998469/). One of them was even reported by users for review. They are very unstable and risky to use because you don’t know what they will do to your system.
Note: Do not download or use the above two extensions. You may end up with an unstable system.
How to use Dolphin as Root
Now you can forget all these hacks and get to run Dolphin as root out-of-the-box with KDE Framework 5.91. The long-pending feature of implementing Polkit support in the KDE Input/Output library (KIO) is finally implemented and merged.
And now, Dolphin and other KDE applications can use KIO to give necessary privileges to perform several non-admin actions.
Steps
Note: As of writing this post, this feature is currently in only Neon Unstable Edition and openSUSE Krypton due to its nature and require more testing before being pushed as stable.
If you are using KDE Plasma using a privileged account already, you are already running Dolphin as admin. But if you are using an account with limited access to the file system, open or use Dolphin as you used to do.
Once you try to modify or access any resources or files via Dolphin that you do not have access to, Dolphin will prompt you for an administrator password via KIO.
To try the code, I tried to modify a file (not admin user) in another user’s (admin) home directory. See the below image. The file opened file. When I am trying to save by the logged-on user (not admin), it prompts for the password, which is nothing but the polkit daemon working via KIO and Dolphin.
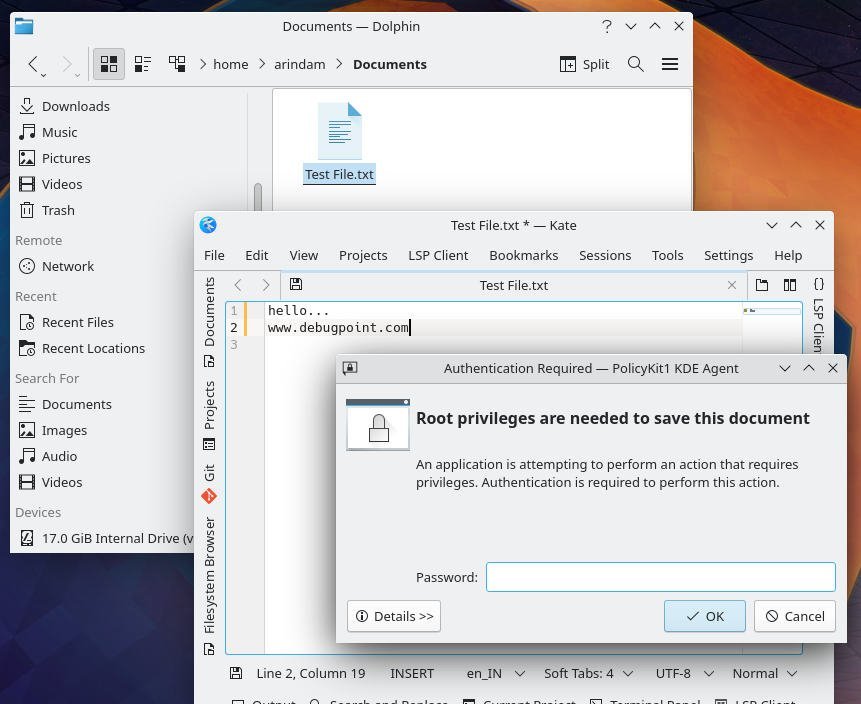
Once you provide the password, you will continue to perform the actions.
I believe this is a very straightforward approach instead of letting users open Dolphin via root separately. Because this limits users to a specific action via admin privileges. It also minimizes the risk of accidentally changing the file system if the entire Dolphin executable is open as root. And opening Dolphin as sudo would give you the same message as earlier with additional instructions below.
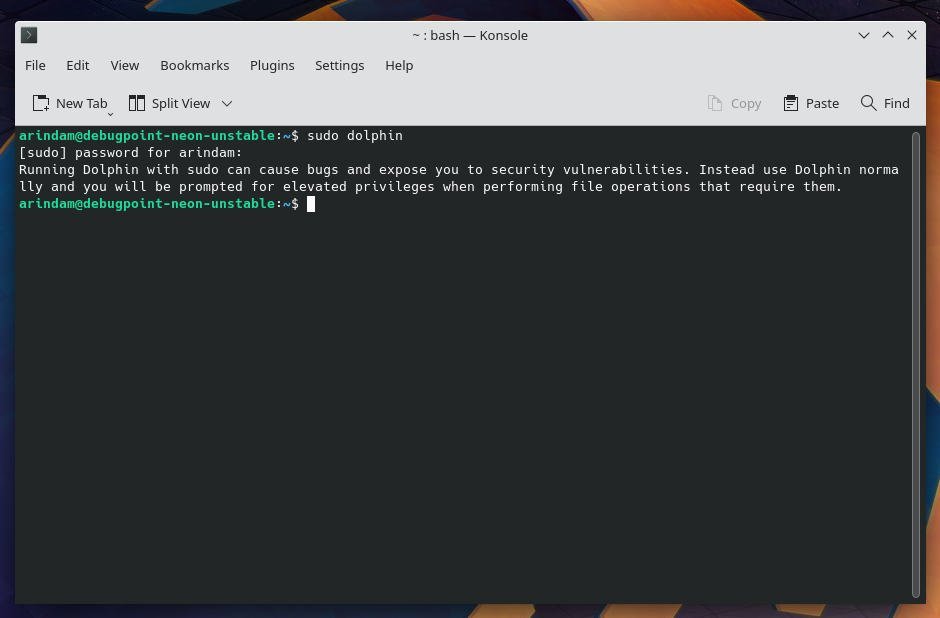
So, that’s about it.
Closing Notes
Dolphin is undoubtedly the famous and best file manager, but this was the missing piece until today. Resolving the “Open Dolphin as the root” problem is significant because it impacts many users system administrators. Thanks to the entire KDE team to pull this through.